What are SPF, DKIM, and DMARC?
- Written by Shane Herring

One of the first challenges to getting marketing emails into a recipient’s inbox is getting past spam filters.
One tactic used to detect spam is to verify that the email was sent by an authorized source.
In this article/video, I give you a closer look at what SPF, DKIM, and DMARC are, how they work, their advantages and disadvantages and how to set them up.
What is DNS?
SPF, DKIM, and DMARC are set up using an organisation’s Domain Name System or DNS tools. DNS is a worldwide database of domain names, such as sbp.com and their corresponding Internet Protocol (IP) addresses (111.222.333.444).
To set up SPF, DKIM, and DMARC, you need access to your organisation’s DNS tool.
Configuring SPF, DKIM, and DMARC involves creating or modifying an organization’s DNS. The type of record is know as a TXT record.
What are SPF, DKIM, and DMARC?
These are a set of free tools that can be used to help email services determine if emails sent on your behalf are trustworthy.
The email content may still be identified as spam but the domain name used will be treated as legitimate.
Why they matter
Here is a real-world example. It happened. I’ve changed the name to protect the guilty.
The client, let’s call her Sandy, has a website and uses Klaviyo to send marketing emails.
When Klaviyo sent an email, email services would try and confirm that those emails were authorized to be sent on Sandy’s behalf. Because there was nothing to indicate that those emails were legitimate, they were delivered but were put into the Spam folder. It was up to the recipient to identify the emails as not spam.
It took only a few minutes to set up SPF, DKIM, and DMARC and the results were immediate. Emails were sent to the Inbox instead of the Spam folder.
What is SPF?
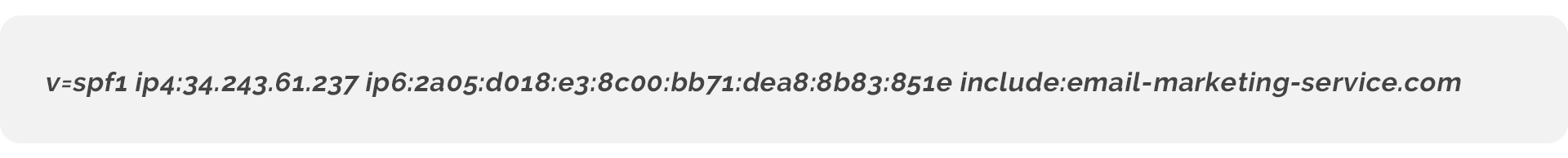
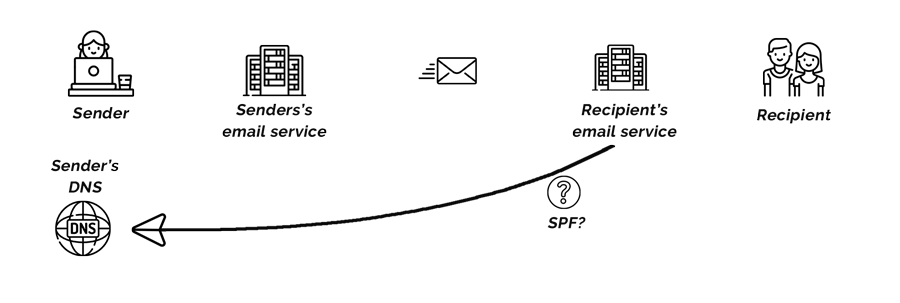
Sender Policy Framework (SPF) is an entry created in an organisation’s DNS. It’s a list of Internet Protocol (IP) addresses or domain names that are allowed to send emails on behalf of that domain. Think of a letter that has a return address. If the recipient, in this case, an email service, knows who sent the letter, it’s more likely to allow it through to an inbox.
How it works
Sandy’s domain is sbp.com.
An SPF record has been created in Sandy’s DNS that authorizes her email service to send emails on behalf of sbp.com.
When an email service receives an email claiming to come from her domain, it checks Sandy’s DNS for a published SPF record. If one exists, it searches that record for an entry that confirms that Sandy’s email service is authorized to send emails on her behalf.
If an SPF record doesn’t exist or there’s no entry authorising the sending service, the receiving service will likely flag the email as spam.
Sandy also uses an email marketing service.
Just like her business emails, when an email is sent from the email marketing service, the from address will be [email protected]. The email is claiming to originate from Sandy’s email service.
She needs to make sure that the SPF record includes an entry for the email marketing service. If there’s no record, it’s likely the emails will be flagged as spam.
Advantages of SPF
- SPF is a basic level of proof that the email comes from a legitimate source.
- If an SPF record or entry doesn’t exist, the email is flagged as spam as quickly as possible.
- Having an SPF record improves the email reputation of the domain and makes it more likely that emails are delivered even if there are other spam indicators.
However, when used without DKIM and DMARC, it has some limitations.
Disadvantages of SPF
- If someone forwards the verified email, the authority of the original email is lost.
- A spammer can send emails that will pass SPF verifications. Combining SPF with DKIM and DMARC reduces this risk.
- Any additional services that will send emails on behalf of a domain must have the SPF record manually updated.
- Only one SPF record is allowed for each domain name. That SPF record can have up to ten DNS lookups. If there are more than 10, the email will fail SPF authentication. If more than 10 are needed, third-party services can help.
- SPF doesn't provide a way to let email services know what to do if an email fails SPF authentication.
How do I create an SPF record?
After the version is the IP address of authorized email servers.
They start with the type of IP address being specified. After the type will be the IP address of the email server. A range of addresses can be specified. More than one IP address can be listed by using the same format. An IP address range may also be used.
So far, an SPF record would look like this.
Next, you may see the domain names of a third-party organization that can send emails on behalf of the domain.
These start with the include: tag.
Typical examples would be email filters or email marketing services. These services should provide the information needed.
More than one include statement can be used but no more than 10.
The record should end with the ‘all’ tag.
The ‘all’ tag defines the policy that should be applied when an email service receives an email from unauthorized sources.
-all (dash all) = This means that servers that aren’t listed in the SPF record aren’t authorized to send emails for the domain and the email should be rejected by the receiving server.
~all (tilde all) = If the sending server isn’t listed in the SPF record, it should not be flat-out rejected by the receiving server. Instead, the message will be marked as possible spam.
+all (plus all) = THIS IS NOT RECOMMENDED. Any domain is authorized to send an email, even if it’s not listed in the SPF record.
Online tools can be used to create or view an SPF record.
MxToolbox is one service that can be used to create or check an SPF record.
Enter the domain name and select Check SPF record.
If an SPF record exists, you see the current record to the right.
MxToolbox’s suggestion for a record is shown to the left.
If you’re not sending emails from your domain, an SPF record should be configured. It’s enough to have v=spf1 -all.
What is DKIM?
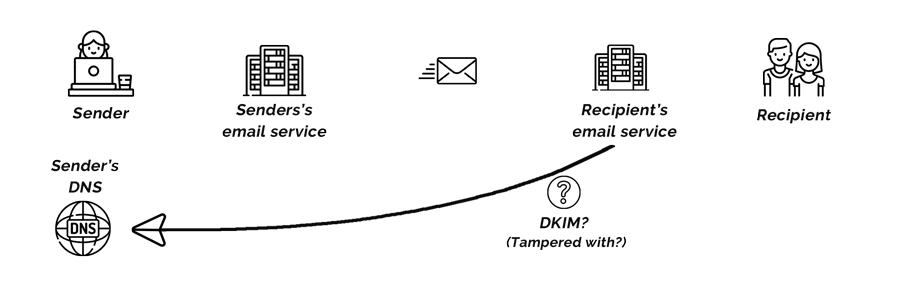
DomainKeys Identified Mail (DKIM) is known as email signing. It exists as an entry in a domain’s DNS.
Like SPF, it acts like the return address. The difference is that it’s like sending a letter using certified or registered mail.
DKIM is a more effective authentication method than SPF because it uses encryption rather than a plain text IP Address.
It’s designed to prove that the email hasn’t been tampered with.
How it works
A DKIM DNS record is what’s known as a TXT entry.
It includes the name of the record and a long string of text. That string is made up of upper and lowercase letters, numbers, and special characters.
When an email is sent from sbp.com, that long text string is encrypted and, along with the name, is included in the outgoing email header.
The receiving email service decrypts the encrypted string and then uses the name to look up the DNS entry.
It compares it with the unencrypted string to the string stored in Sandy’s DNS.
If they match, two things are known:
- the encrypted string was not changed in transit
- the service that added the encrypted text string sent the email.
Advantages of DKIM
- DKIM is a stronger authentication method than SPF since it uses an encrypted text string.
- If the recipient forwards the email, the encrypted string is kept with the email message. This can help reduce the chances of the email being identified as spam.
- It makes it difficult for spammers to make the email appear as though it came from an authorized source.
Disadvantages of DKIM
- Like SPF, DKIM doesn’t let email services know what to do if the authentication checks fail.
- There can be issues when the relay or filtering program changes the messages.
- A determined person can still create an email that appears to be from an authorized source.
How do I create a DKIM record?
Like SPF, an email service may create a DKIM record automatically.
A business can have more than one DKIM record.
If you’re using third-party services to send emails on your behalf, such as an email marketing service, you will have to add an additional DKIM record.
Those third-party services will usually generate the record details which you copy and paste into your DNS management tool.
The name of this type of record with be the organization’s domain name with a prefix. The first part of that prefix is known as a selector. Following the selector is the indicator that identifies the record as a DKIM record.
For a DKIM record in Sandy’s DNS, the name is default._domainkey.sbp.com.
default is the selector. _domainkey indicates that the record is a DKIM record.
Another common selector is dk.
A DKIM record requires a ‘p’ tag.
p= specifies the string that will be encrypted by the sending email service and the string that the receiving service uses after decryption.
Other commonly used tags include:
v= indicates the version of DKIM being used. Currently, always version 1.
k= indicates the encryption method being used. For example, k=rsa.
Other tags may be used.
Because encrypted text needs to be included in outgoing emails, use the details provided by your email provider or third-party services.
To confirm the DKIM records for a domain, use tools such as the MxToolbox DKIM record lookup tool.
Enter the domain name and selector.
If you don’t have access to your DNS, you can find out what the selector is by sending an email to yourself.
View the email header and search for the line beginning with “DKIM-Signature”. The s= tag will have your selector as its value. Your DNS may be configured with more than one DKIM record, each with a unique selector.

What is DMARC?
Domain-based Message Authentication, Reporting and Conformance (DMARC) is an email authentication method that uses SPF and DKIM to decide whether an email is authentic.
It has three basic purposes:
- It verifies that a sender’s email messages are protected by both SPF and DKIM.
- It tells the receiving mail server what to do if validation fails with either SPF or DKIM.
- It provides a way for the receiving server to report back to the sender about messages that pass and/or fail the DMARC evaluation.
Since DMARC uses both SPF and DKIM, you may wonder why it’s even necessary. Well, it’s simple: DMARC builds on SPF and DKIM to ensure that, when an email is received, the information contained in both records matches the “friendly from” domain (e.g., [email protected]) that the user sees and the From address that’s contained in the message’s header.
DMARC is very effective because it validates the sender of an email using both DKIM and SPF records. Furthermore, it assists mail systems in deciding what to do with messages sent from your domain that fails SPF or DKIM checks.
How it works
Sandy has entries in her DNS for SPF, DKIM, and DMARC.
She sends an email.
The receiving email service checks the SPF record to validate that the sending service is allowed to send an email on Sandy’s behalf.
If it is, the receiving service checks the DKIM record to ensure that the message hasn’t been tampered with and was actually sent by the sending service.
If the email passes both checks, the service will then check the email content for spam indicators.
If the email fails either the SPF or DKIM validation, the DMARC record is checked to determine what action to take with the email.

Advantages of DMARC
- DMARC allows organisations and domain owners to receive reports on the email messages they send.
- Having control over your stream of email messages increases trust and adds more value to the messages you send.
- Make your email easily identifiable across the network of DMARC-capable receivers.
Disadvantages of DMARC
- Sometimes, legitimate messages can be blocked or marked as spam.
How do I create a DMARC record?
DMARC is not typically created by an email-sending service. But that’s ok. It’s not hard to create.
As mentioned, DMARC allows the domain owner to specify how an email service should handle emails that fail validation. It uses what is called a policy.
To use DMARC, you must have SPF and DKIM configured.
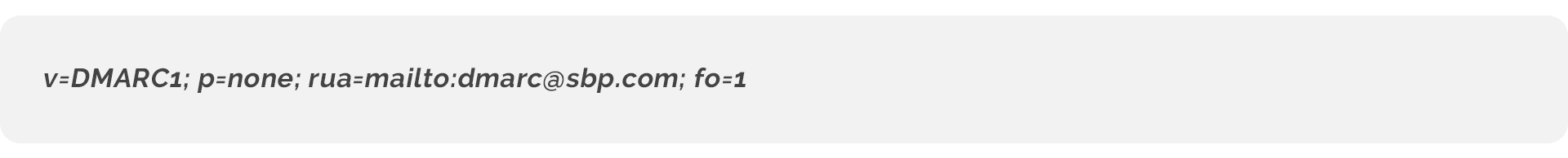
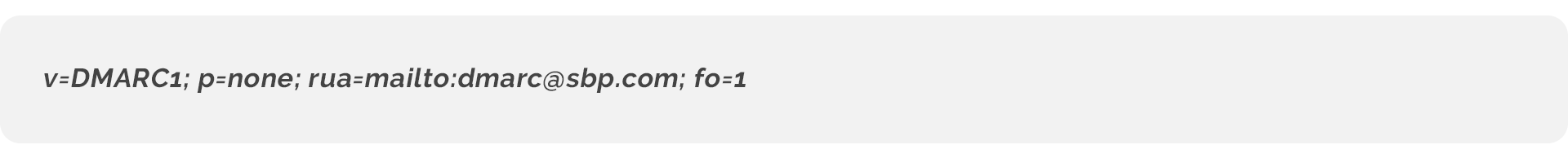
A DMARC record has a specific DNS record name.
For example, DMARC.sbp.com. Like SPF and DKIM, the name helps the receiving email service find a DMARC record.
Only two tags are required for a DMARC record.
The version which starts with v=.
Next is the DMARC policy tag, p=
Policies are used to let a receiving email service know what to do with emails that fail a validation check.
The three policies are:
p=none; no action is taken, and the message is delivered as usual.
p=quarantine; sends the message to the spam/junk/quarantine folder
p=reject; sends the message back to the server that sent it.
If the validation fails, the necessary action is taken based on the policy defined in the DMARC record.
Optional but recommended tags are:
rua= tells receiving servers where to send daily reports. I recommend setting up a dedicated email address for this.
fo= lets receiving email servers know that samples of messages that fail either SPF and/or DKIM should be returned to the sender. There are four value options for this tag:
fo=0: Generate a DMARC failure report if both SPF and DKIM fail to produce a “Pass” result. This is the default option.
fo=1: Generate a DMARC failure report if both SPF and DKIM produce something other than a “Pass” result. This is the recommended option.
fo=d: Generate a DKIM failure report if the message had a DKIM signature that failed the evaluation, regardless of why.
fo=s: Generate an SPF failure report if the message failed SPF evaluation, regardless of why.
Even though DMARC isn’t widely adopted by email services, you should use it.
It shows email services that you are an actual sender who is willing to take precautions to protect your identity and reputation.
If you want a report showing the emails that aren’t passing the SPF and DKIM verification checks and don’t want to block any emails, use this setting.
The easiest way to create your DMARC record is using a tool such as MxToolbox.
Not only can MxToolbox’s DMARC record generator create your record, but you can also include MxToolbox as a recipient of the daily emails. The site will help analyse the results.
Are all three required?
No. All three are not required.
You can use SPF without using DKIM or DMARC. You can use DKIM without SPF or DMARC. To use DMARC, you need SPF and DKIM. DMARC is still something that is taking a while to catch on.
Having said that, why would you not use all three? There is no overlap. They complement each other.
Using all three shows that your email domain is truly who it claims to be. It shows that your organisation is serious about following best practices and that you’re doing your part to prevent spam, phishing, and other email security issues.
Wrap up
SPF, DKIM, and DMARC are essential in showing that emails sent on your behalf are authorized.
SPF can list who can send emails on your behalf.
DKIM checks that the emails haven’t been tampered with.
DMARC specifies what to do with emails that fail validation.
Use all three to build trust and show you’re serious about preventing spam.
Let us know about your experiences with SPF, DKIM, and DMARC. Have they helped to get your emails through spam filters?
Head over to the Atomic Education Facebook page and join the conversation.

Shane
Like this article? Share it